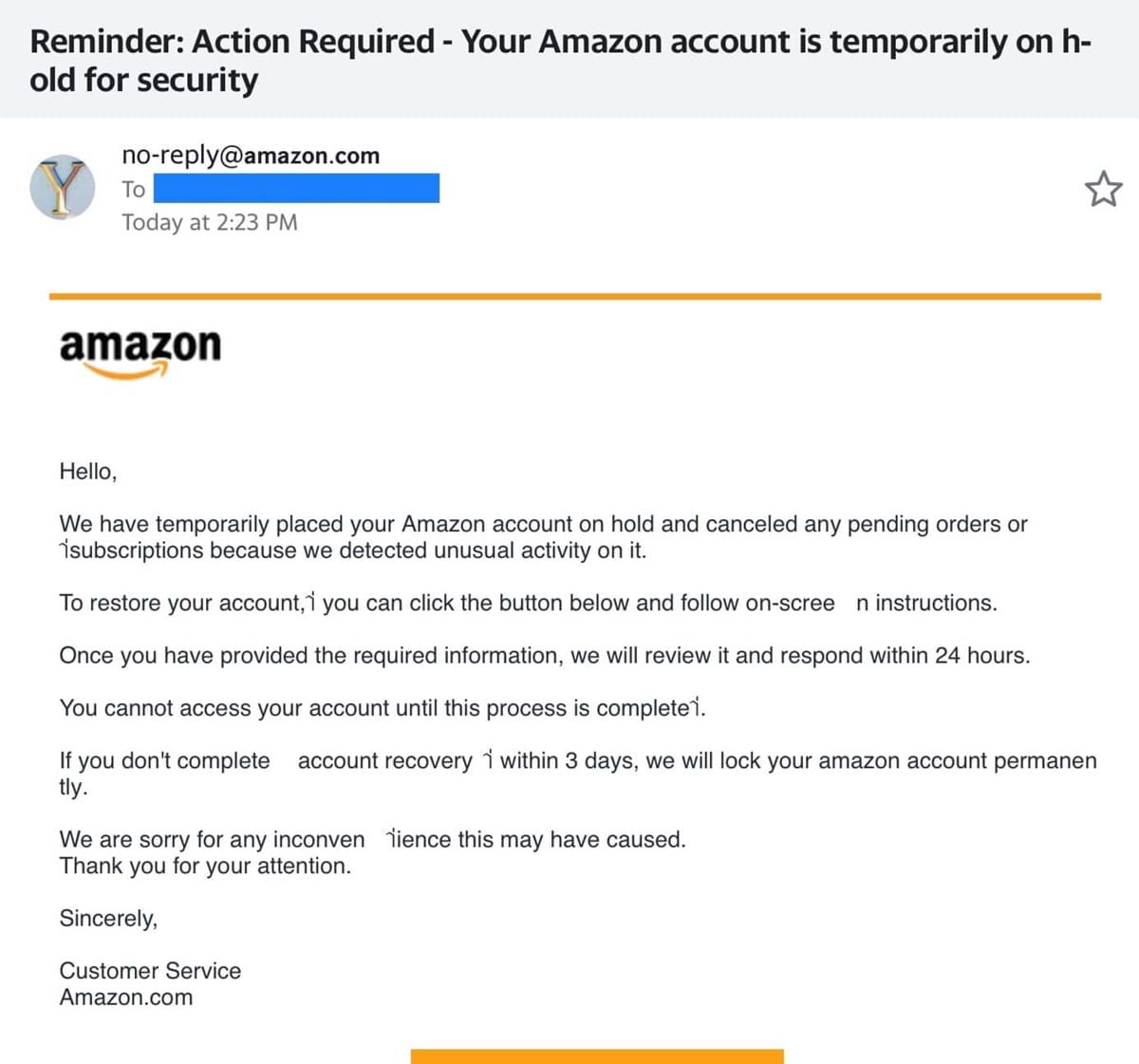
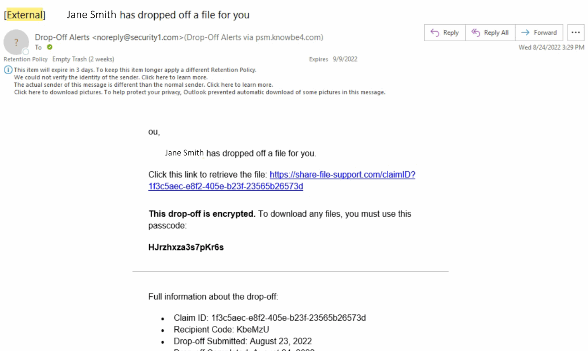
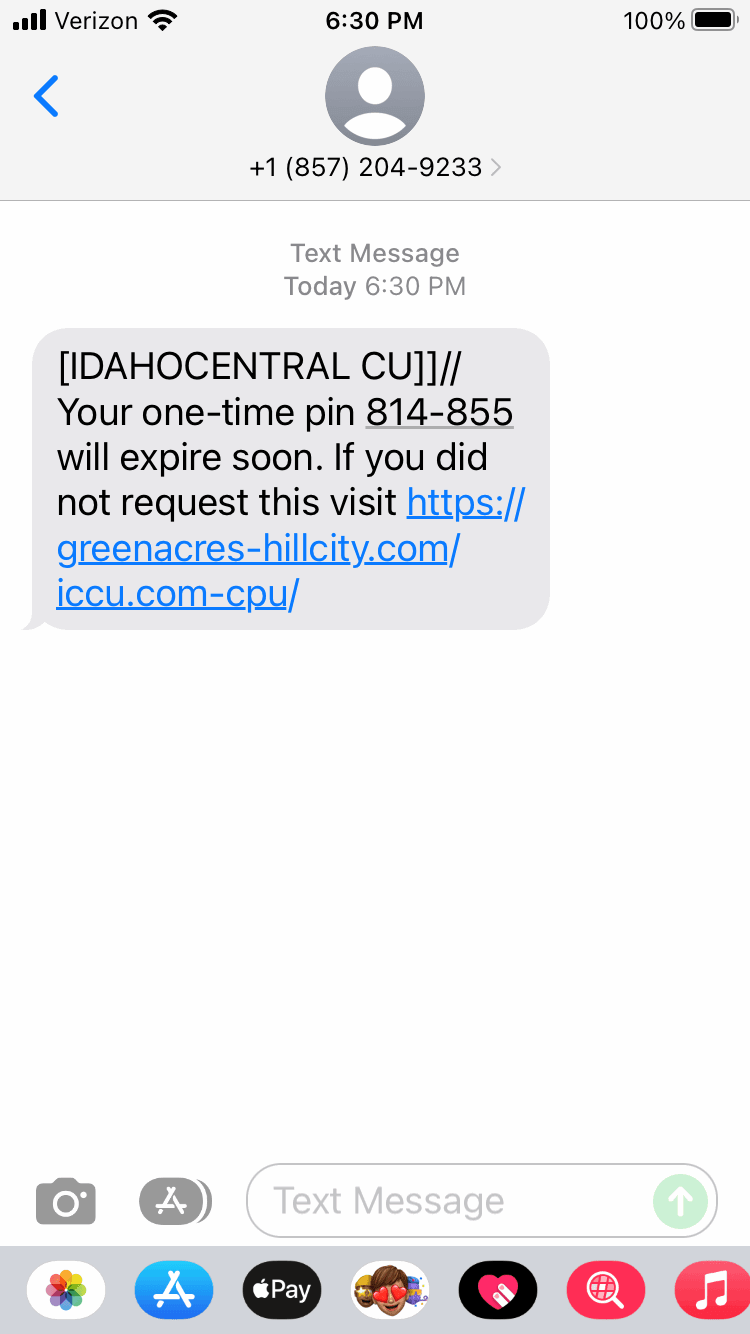
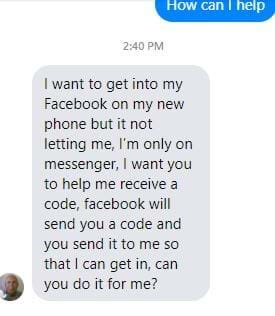
3. Phishing: The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
Phishing sites go after millions of people as a random attack. These emails are made to look like they came from a known reputable source. The content of the email is about an action required and is usually a response to “suspicious activity” on your account, or alerting you of a purchase you did not make. The email will likely say External in the subject line and will not be from the email you know. But it is designed to instill a quick fear reaction. There are multiple iterations of how the scam will play out depending on the target's response. The email could contain Spyware that infects your computer, take you to a site where you need to enter personal and banking information, or provide a number to call which is to the scammer.
4. Spear Phishing: The fraudulent practice of sending emails ostensibly from a known or trusted sender in order to induce targeted individuals to reveal confidential information.
The circumstances are similar to a Phishing Scam but in this case the scam is more target. The scammer has likely done some research online or through social media and will use that information to manipulate you. The email may look like it’s coming from a coworker or loved one.
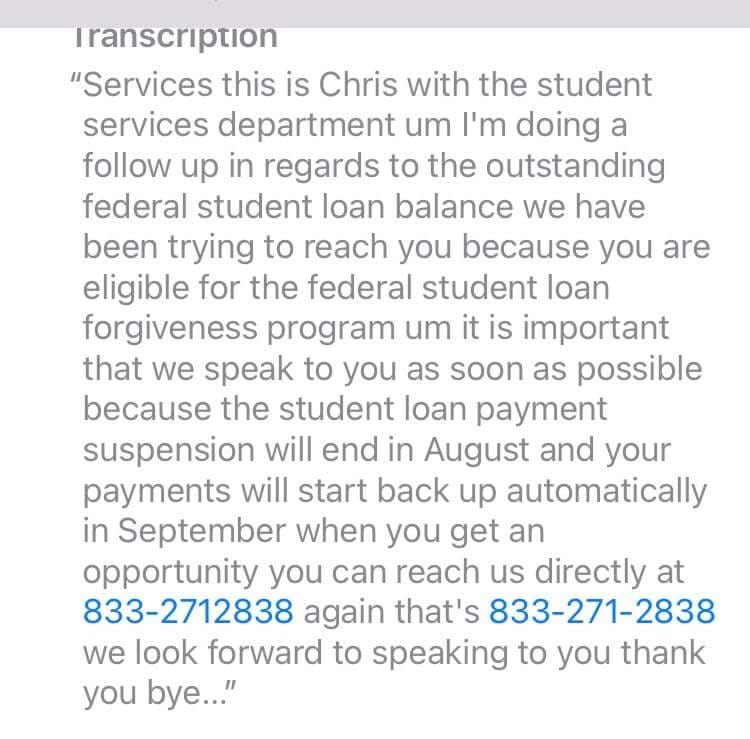
5. Vishing: The fraudulent practice of making phone calls or leaving voice messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as bank details and credit card numbers
If you get a robocall that's vishing. Any kind of call where the person is threatening you for money ( warrant scams, grant scams, grandparent scams, etc.) is vishing.
6. Smishing: The fraudulent practice of sending text messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords or credit card numbers.
This also applies to scams done through social media with fraudulent links, verification notices or request to share data with someone online.
- Never call numbers provided in these messages. Look them up yourself and call the actual business.
- Never click a suspicious link.
- If the email is just a name hover the cursor over the name to see the actual email address.
- Always question, and then confirm before clicking or providing money or information due to an email, call or text.